Hosting AWS VPC Interface Endpoints in Shared Model
What is VPC Endpoint
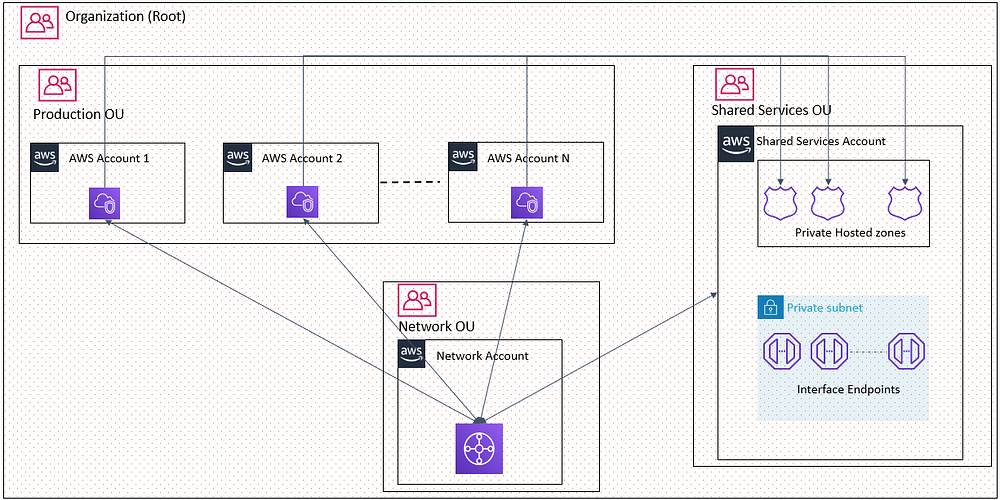
Do you have Multi AWS Accounts in Organization?
When you have multi accounts structure in your Organization then creating endpoints in each accounts will increase the costs and IPs, in this blog I will explain how you can deploy endpoints in Shared Services Account and associate the member accounts VPCs with Private Hosted zone.
 |
|
|
AWS Services/Components required
- VPC
- Subnets
- Endpoints
- Hosted zone and Record set
- Transit Gateway
Implementation Steps
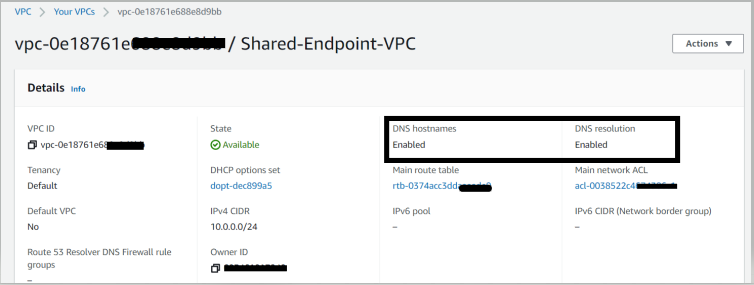
- Create a VPC in shared services account and enable DNS hostname and resolution. Create the Subnets as per your requirement
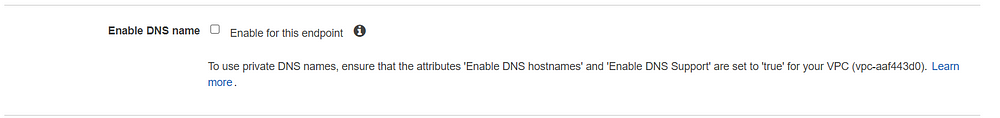
- Create required VPC endpoints and based on the HA setup, select required subnets to have endpoints hosted. Don't check or enable DNS name
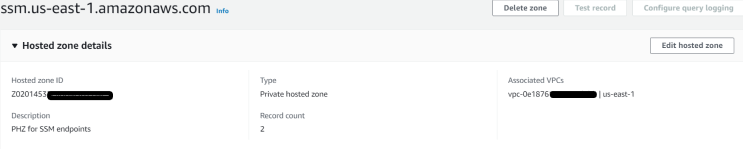
- Create Private hosted zone with exact DNS name of the endpoints name, some DNS name will not have same as endpoints name, like for ecs agent, DNS name is “ecs-a.${AWS::Region}.amazonaws.com” and for ecs telemetry its DNS name is “ecs-t.${AWS::Region}.amazonaws.com” so make sure the DNS name is accurate in Private hosted zone
- Create an “A” record and choose regional VPC endpoints for traffic to route
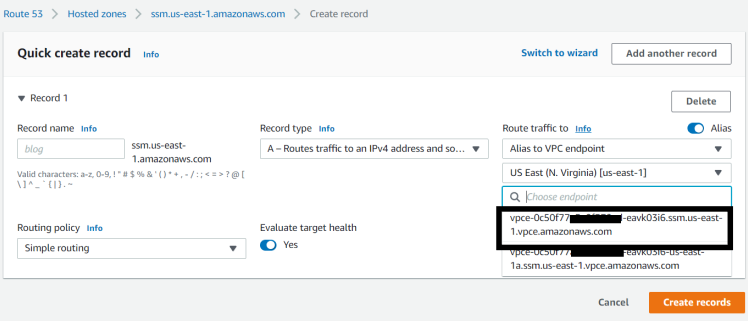
Associate a Route 53 private hosted zone with a VPC in a different AWS account
- From network account, where TGW is configured, you have to share the TGW to both production account and Shared account, also its possible to share to the OU, since Network account is part of same Organizations. Create the Transit gateway attachments in Shared and Prod account with the shared TGW. Configure the routes in Network account to have connectivity between shared and prod accounts
Testing
Launch an EC2 instance in prod account and run nslookup ssm.us-east-1.amazonaws.com in cmd where it will resolve Shared service Endpoints Subnets IP address and without hosting endpoints in production account, it resolved SSM endpoints privately
 |
| DNS resolved shared services endpoint for ssm |
Traffic Flow
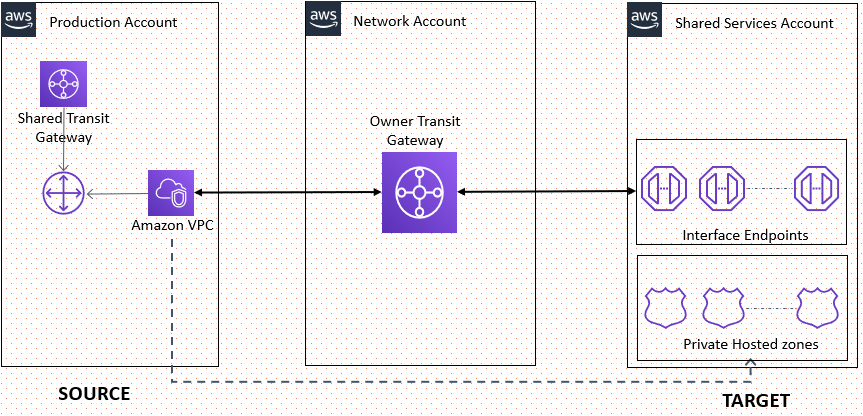 |
| Design Workflow |
How it works?
When you try to access VPC endpoint, say ssm.us-east-1.amazonaws.com then first AWS VPC DNS checks the associated PHZ in Shared account then it will connect to Shared services VPC endpoints through Transit Gateway and do the operation and traffic will be internal.
Limitations
Throughput:
Each Endpoint ENI can sustain 10Gbps with bursts up to 40Gbps and TGW provides 10 GbpsVPCs per Private Hosted Zone:
By default, 100 VPCs can be associated with Private hosted zone and hard limit is 1,0001000 VPCs can be associated with a single Private hosted zone. We can create a new private hosted zone for the endpoint which will have a unique zone ID and associate the 1001 VPCs to the new private zone, so that there will be no limitation in VPC association.
VPC Interface Endpoints per VPC:
Default is 50 but it can be increased to include all AWS services that have VPC endpoints.Endpoint Policy Length:
Hard limit of 20,480 characters, important if you plan to use custom policiesAdvantages
- Host Endpoints only in Shared Services account
- Establish secure private connection towards AWS service for multiple VPCs
- Have minimal cost impact to provide this connection
- Saves huge number of IP space
- Finally, save huge number of $
Comments
Post a Comment